LOG Threat Detection and Response
as a service
V Logs from security devices, applications and cloud
environments can give you the most powerful data you can get.
To know your next step you need to know where you are today. Your profile as an organisation, your risk appetite and specific regulations are just a few of the business drivers that will help you to make that decision. The layers and the type of protection, detection and response is unique for every business. What’s right for you doesn’t need to be complex.
Need to discuss your business cyber security further?
Chat with us online now! We can answer your IT support questions quickly, so you get the information you need.
Cutting Edge SIEM
What you want from Endpoint Detection and Response, is a solution that helps you correlate events across machines as well as on machines themselves, to push alerting speed and precision to a new level and at the same time an enterprise-wide view.
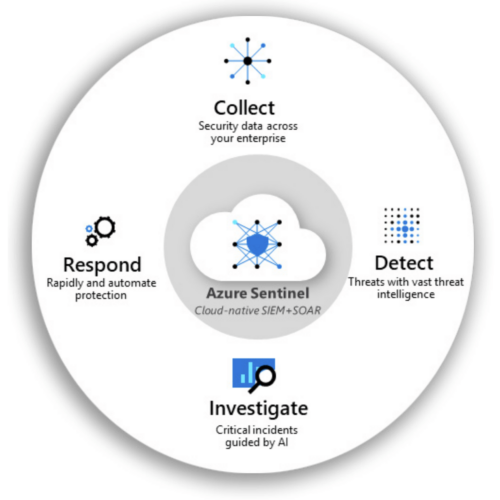
Azure Sentinel is a cost-effective way to simplify and modernise your security operations. Collect security data from across your entire organisation and monitor it in one central location, giving you a bird’s eye view so it’s easier to spot suspicious activities and effectively deal with threats quickly.
The machine learning models are based on decades of learnings from the Microsoft security team, and with trillions of signals across the globe fed in daily, its capabilities are unparalleled in the market. Sentinel connects the dots for you when it comes to threat detection.
Is it for my business?
Challenges
- Management and continuous improvement of log based detection and response platform.
- Staffing a security platform management team with subject matter experts
- Lack of resources to staff a Security Operations Centre (SOC) 24×7
- Developing detection use cases that provide enough context for analysts without producing “alert fatigue”.
- Applying global intelligence to cyber security threats.
When should you consider it?
- If you have compliance requirements that require log storage, which you want delivered as a service.
- If you require experts to help deploy and run an outcome-based managed detection and response service based on SIEM.
- If you require 24×7 or 8×5 managed threat detection.
- If you require a provider that not only provides Log based Detection and Response but also Endpoint and Network based detection as well as comprehensive cyber threat intelligence
What do we do?
- Deployment of our proprietary Pattern-based detections to the Sentinel platform.
- Continuous incident triage, analysis, and prioritisation by security analysts.
- Custom use case / detection development.
- Support, Change Management, Upgrades and Patching and log source integration.
- Performance, Device Health, OS, Log Source, Application and License Monitoring.
What will you get?
- A fully managed SIEM platform.
- Real-time incident analysis.
- Monthly security and operational reporting.
- Cyber threat hunting.