Endpoint Detection and Response (EDR)
as a service
Visibility across your business is key and the endpoint is the quickest way to get it.
There is no such thing as 100% protection. Once you have accepted this fact it is time to implement a strategy on how to detect the threats you couldn’t prevent. The challenge with detection is that today’s threats are not using old malware that is easy to detect and remediate. This behaviour needs to be analysed and correlated across other endpoints to be able to separate the false positives from the real incidents.
Need to discuss your business cyber security further?
Chat with us online now! We can answer your IT support questions quickly, so you get the information you need.
How the EDR service works
and how we help protect your business
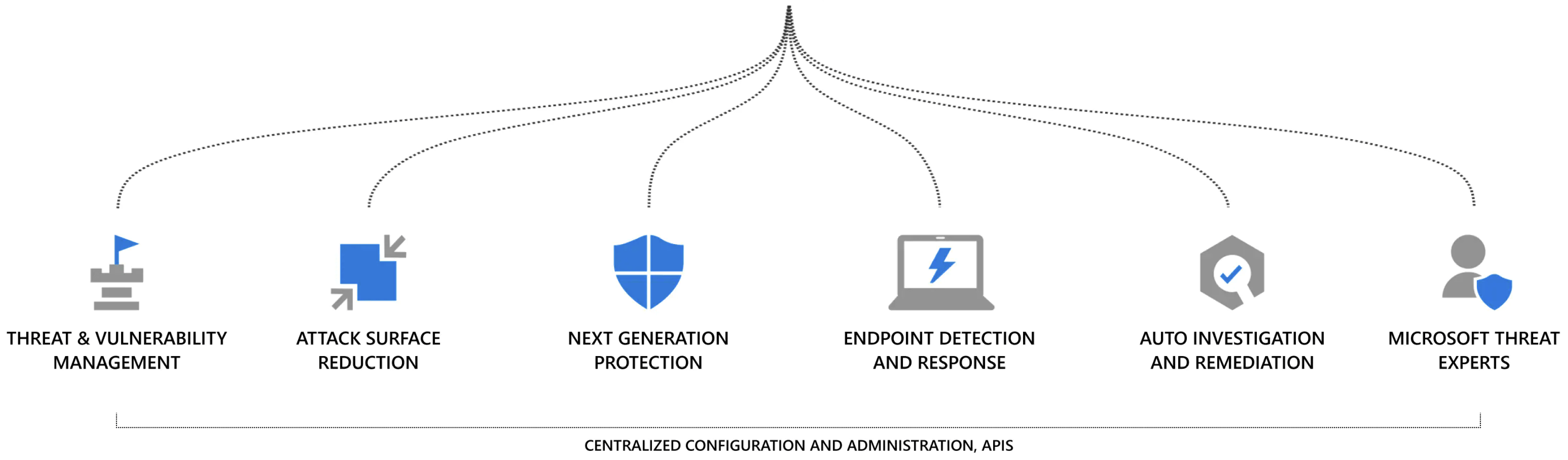
What you want from Endpoint Detection and Response, is a solution that helps you correlate events across machines as well as on machines themselves, to push alerting speed and precision to a new level and at the same time an enterprise-wide view.
EDR
Endpoint Detection and Response
Is it for my business?
Challenges
- Lack of resources to staff your Security Operations Centre 24×7.
- Continuous management of EDR configuration to ensure enough context for analysts without producing “alert fatigue”.
- Applying global intelligence to cyber security threats.
- Lack of visibility and control of endpoints.
When should you consider it?
- If you require experts to help deploy and run an outcome-based managed detection and response service based on EDR.
- If you require 24×7 or 8×5 managed threat detection.
- If you require a provider that not only provides Endpoint Detection and Response but also Log and Network based detection as well as comprehensive Cyber Threat Intelligence.
- If you require integration of cyber security tools.
- If you require additional Managed Threat Response capabilities.
What do we do?
- Deployment of Microsoft Defender for Endpoint platform.
- Platform management of Microsoft Defender for Endpoint EDR.
- Continuous incident triage, analysis, and prioritisation by security analysts.
- Managed Threat Response such as isolation of infected endpoints.
- Integration of Cyberdefense unique Threat Intelligence custom EDR rules (Premium/scoped)
What will you get?
- Fully managed EDR platform operations.
- Monthly reporting to gage effectiveness of the solution.
- Real-time incident analysis and endpoint active response.
- Optional cyber threat hunting (Premium/Scoped)